Enterprise-Grade Cybersecurity for a Secure Digital Future
Protect your infrastructure, cloud, and data with next-gen security solutions built to detect, prevent, and respond to threats in real-time. Stay ahead of cyber risks with Pentora the modern alternative to legacy security platforms.
Our Expertise
Comprehensive Solutions
Full-spectrum services: assessments, threat intel, compliance & response readiness.
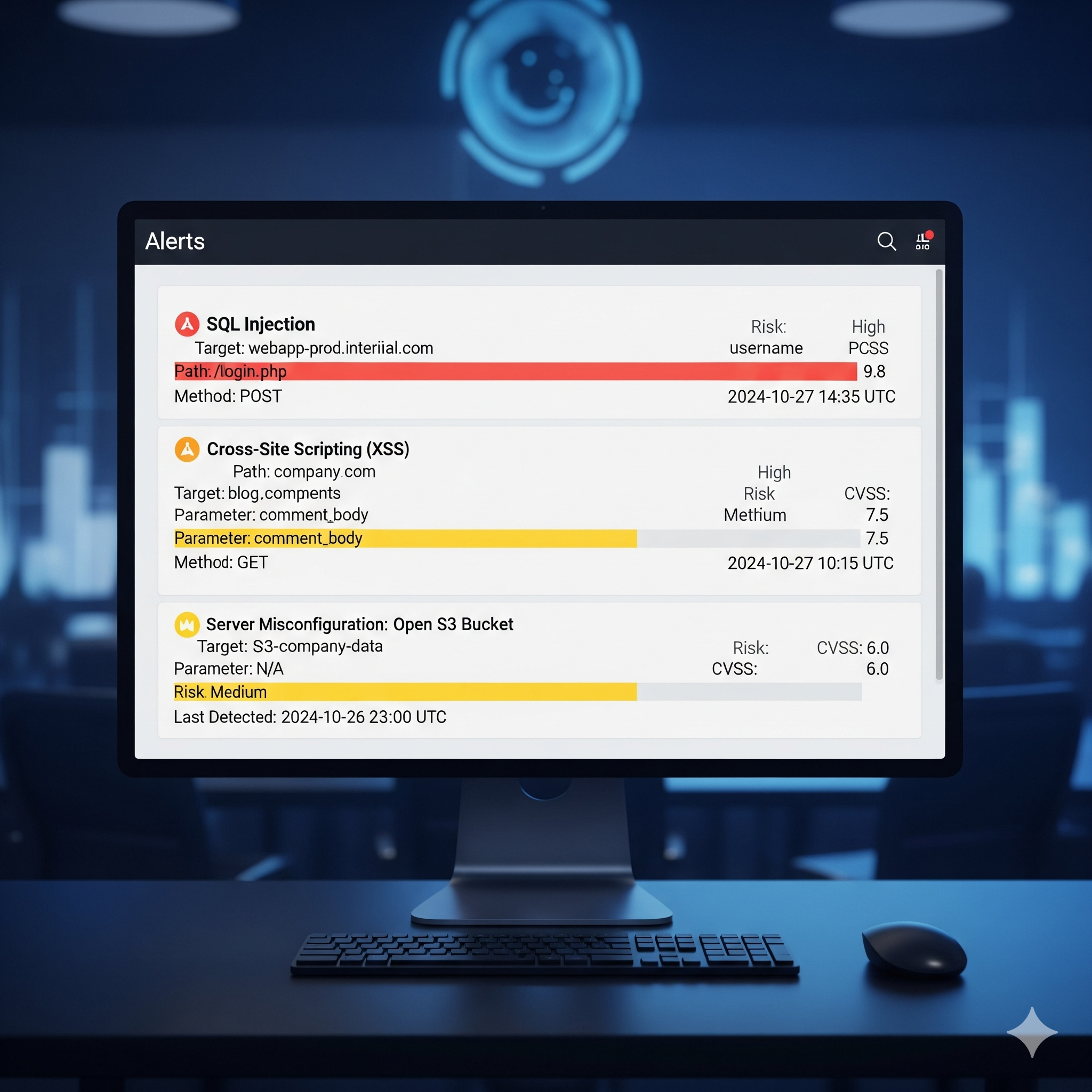
Application Security & VAPT
Identify and remediate vulnerabilities in your applications before they can be exploited by malicious actors.
PENTORA
Secure Your Data, Secure Your Future.
Live Global Threat Analysis
Our Security Operations Center (SOC) monitors global threats 24/7, providing real-time insights and immediate response capabilities.
Why Choose Us?
We prioritize security from the start to ensure customer workloads are always protected. Our expert services offer a security-first approach to safeguard your valuable assets.
AI Analyst Co-Pilot
Leverage our generative AI to automate investigation summaries, write response plans, and query data with natural language.
Our Unique Approach To Security
We offer a comprehensive suite of cybersecurity services designed to protect your organization's critical assets and reputation.
Penetration Testing
We identify vulnerabilities and assess the overall security posture.
Threat Monitoring
We monitor and analyse your company and respond to security threats in real-time.
Response Assessment
We evaluate security incidents and develop effective response plans.
Cloud-Native Security
Secure cloud environments to protect data and applications during migration and beyond.
Data Security
Comprehensive solutions to safeguard sensitive data, including encryption and access control.
Security Automation
Streamlined security operations to help you respond to threats quickly and effectively.
24/7 Global Operations
AI-Powered Global Security Operations Center
Our GSOC is the nerve center of our defensive capabilities, providing continuous monitoring, advanced threat detection, and rapid response across the globe.
0
Threats Neutralized Today
Real-time analysis and mitigation of malicious activities.
0
Assets Under Protection
Endpoints, cloud instances, and networks actively monitored.
0
Active Incidents
High-priority security events currently under investigation.
Live Threat Feed
APT28 Activity
EMEA Financial Sector
Neutralized
Zero-Day Exploit
APAC Cloud Provider
Patched
DDoS Attempt
NORAM E-commerce
Mitigated
Ransomware Signature
Global Logistics Network
Blocked
Phishing Campaign
LATAM Healthcare
Contained
APT28 Activity
EMEA Financial Sector
Neutralized
Zero-Day Exploit
APAC Cloud Provider
Patched
DDoS Attempt
NORAM E-commerce
Mitigated
Ransomware Signature
Global Logistics Network
Blocked
Phishing Campaign
LATAM Healthcare
Contained
OUR IMPACT
AI-Driven Security in Action
See how our tailored solutions help global leaders in finance, tech, and critical infrastructure defend against the most advanced cyber threats.
1 of 3
Predictive Threat Modeling
Objective: Leveraged AI to analyze global networks, predicting and neutralizing zero-day exploits targeting SWIFT transfers.
Dark Web Monitoring
Objective: Proactively monitored dark web marketplaces for stolen credentials of a major retail client, leading to the takedown of a major phishing operation.
Geopolitical Risk Analysis
Objective: Provided real-time threat intelligence on geopolitical events for a global logistics company, avoiding supply chain disruptions.
99.7%
Predictive Accuracy
Achieved near-perfect accuracy in identifying potential zero-day exploits.
<1 Min
Global Alert Time
Threat intelligence disseminated to all clients in under 60 seconds.
WHAT ALL WE DO
Our Unique, Best Approach To Systems Implementation
We offer a comprehensive suite of cybersecurity services designed to protect your organizations critical assets and reputation.
Application Security
Comprehensive solutions to protect against external threats and prevent unauthorized access to sensitive data.
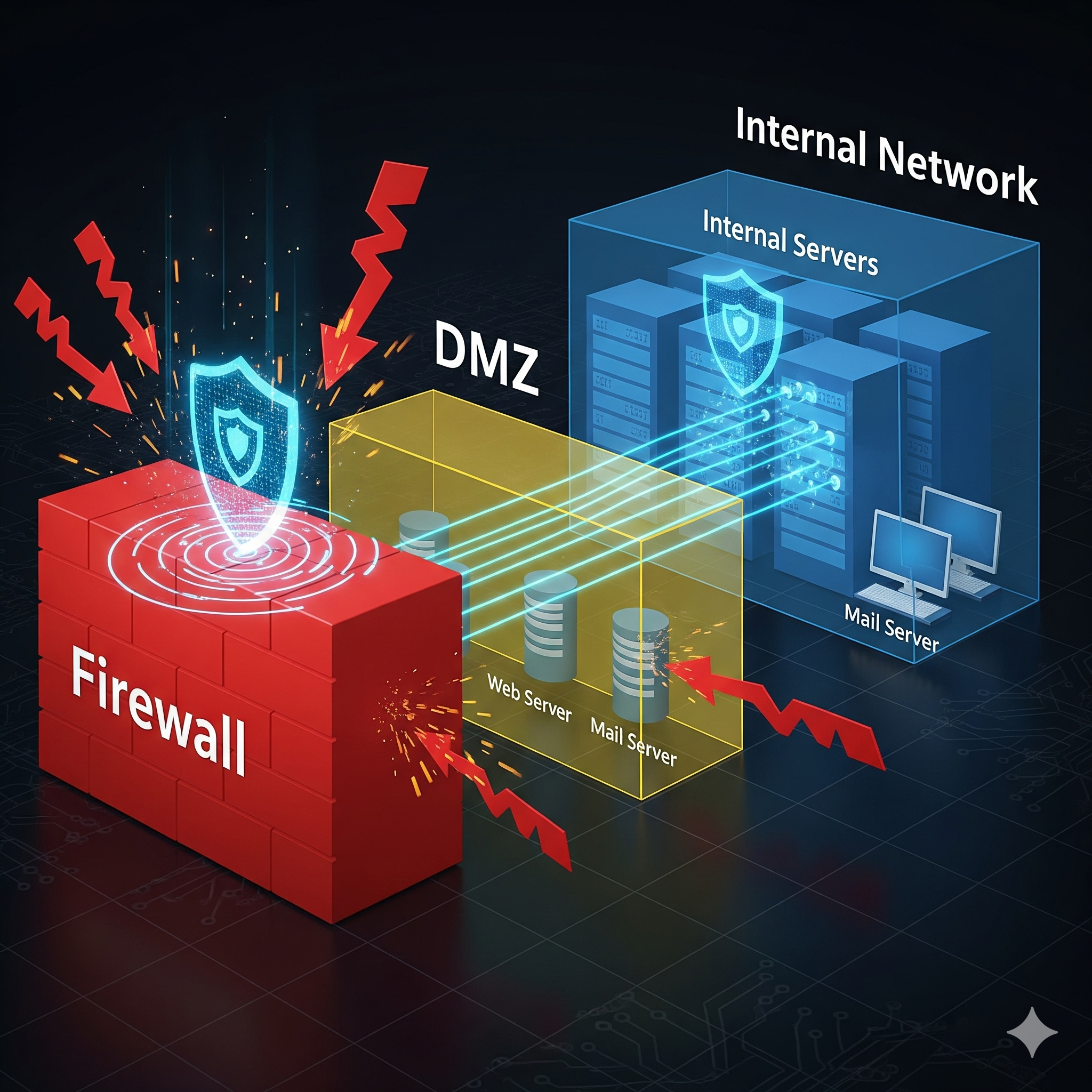
Network Security
Customized solutions to prevent unauthorized access, monitor network activity, and respond to threats in real-time.
Cloud-native Security
Secure cloud environments to protect data and applications during migration and beyond.
Data Security
Comprehensive solutions to safeguard sensitive data, including data classification, encryption, and access control.
Security Automation
Streamlined security operations to help you respond to threats quickly and effectively.
Infrastructure Security
Secure infrastructure solutions to protect against external and internal threats.
